Computers and Technology, 19.05.2021 19:10, uverworldxdz4999
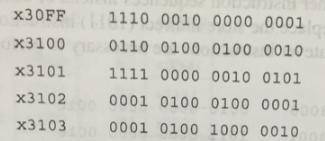
Suppose the following LC-3 program is loaded into memory starting at location
x30FF: x30FF 1110 0010 0000 0001
x3100 0110 0100 0100 0010
x3101 1111 0000 0010 0101
x3102 0001 0100 0100 0001
x3103 0001 0100 1000 0010
If the program is executed, what is the value in R2 at the end of execution?

Answers: 3
Other questions on the subject: Computers and Technology

Computers and Technology, 22.06.2019 03:50, TheViperMlg23676
You are working as a security analyst in a company xyz that owns the whole subnet range of 23.0.0.0/8 and 192.168.0.0/8. while monitoring the data, you find a high number of outbound connections. you see that ip's owned by xyz (internal) and private ip's are communicating to a single public ip. therefore, the internal ip's are sending data to the public ip. after further analysis, you find out that this public ip is a blacklisted ip, and the internal communicating devices are compromised. what kind of attack does the above scenario depict?
Answers: 3

Computers and Technology, 22.06.2019 08:00, lindseyreneesmith7
Digital information is stored using a series of ones and zeros. computers are digital machines because they can only read information as on or off –1 or 0. this method of computation is known as the system
Answers: 1


Computers and Technology, 23.06.2019 11:30, talyku7131
Me dangers of social media and the internetexplain what each means: 1) social media and phones have become an addiction.2) outside people have access to you all the time.3) cyberstalking4) cyberbullying5) catphishing6) viruses7) identity theft8) credit card fraud9) hacking10) money schemes
Answers: 1
Do you know the correct answer?
Suppose the following LC-3 program is loaded into memory starting at location
x30FF: x30FF 1110 001...
Questions in other subjects:











![R[1]](/tpl/images/1334/2761/df90b.png)
 .
.