
Computers and Technology, 30.04.2021 02:50, crawford184232323234
Explains in detailed steps how the algorithm implemented in the identified procedure works. Your explanation must be detailed enough for someone else to recreate it.
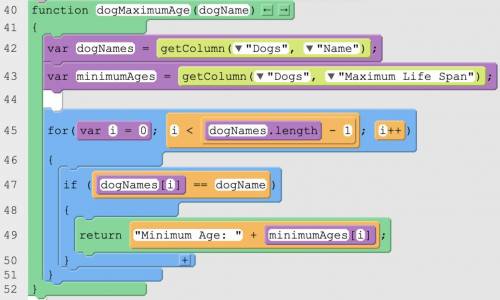

Answers: 2
Other questions on the subject: Computers and Technology

Computers and Technology, 22.06.2019 08:30, ruddymorales1123
Linda subscribes to a cloud service. the service provider hosts the cloud infrastructure and delivers computing resources over the internet. what cloud model is linda using
Answers: 1

Computers and Technology, 22.06.2019 10:10, joanasprinkman2262
3. bob is arguing that if you use output feedback (ofb) mode twice in a row to encrypt a long message, m, using the same key each time, it will be more secure. explain why bob is wrong, no matter what encryption algorithm he is using for block encryption (15 points).
Answers: 3


Computers and Technology, 23.06.2019 09:00, jeremytheprimerapper
Which best compares appointments and events in outlook 2010appointments have a subject man, and events do notappointments have a specific date or range of dates, and events do notappointments have a start and end time of day, and events do notappointments have a location option, and events do not
Answers: 2
Do you know the correct answer?
Explains in detailed steps how the algorithm implemented in the identified procedure works. Your exp...
Questions in other subjects:



Mathematics, 22.01.2021 23:40


Chemistry, 22.01.2021 23:40

History, 22.01.2021 23:40

Biology, 22.01.2021 23:40

Physics, 22.01.2021 23:40

Mathematics, 22.01.2021 23:40






