Find what the secret message is. Get Brainliest if you are fast and correct.
...

Computers and Technology, 15.04.2021 18:10, onewaydemon
Find what the secret message is. Get Brainliest if you are fast and correct.
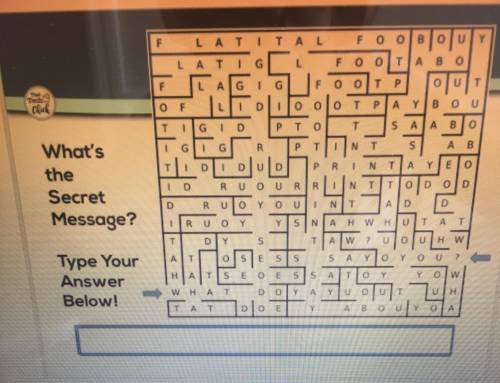

Answers: 1
Other questions on the subject: Computers and Technology

Computers and Technology, 22.06.2019 10:40, Morghurley2000
"it security policy enforcement and monitoring" respond to the following: describe how monitoring worker activities can increase the security within organizations. describe the rationale that managers should use to determine the degree of monitoring that the organization should conduct. explain the extent to which you believe an organization has the right to monitor user actions and traffic. determine the actions organizations can take to mitigate the potential issues associated with monitoring user actions and traffic.
Answers: 3

Computers and Technology, 23.06.2019 10:30, badpotterchris
How would you categorize the software that runs on mobile devices? break down these apps into at least three basic categories and give an example of each.
Answers: 1

Computers and Technology, 23.06.2019 18:40, cyn95xx
Johnson enterprises uses a computer to handle its sales invoices. lately, business has been so good that it takes an extra 3 hours per night, plus every third saturday, to keep up with the volume of sales invoices. management is considering updating its computer with a faster model that would eliminate all of the overtime processing.
Answers: 2

Computers and Technology, 23.06.2019 22:30, reaganphelps3
What would be the address of the cell, which is at the intersection of the second row and the third column in a worksheet?
Answers: 1
Do you know the correct answer?
Questions in other subjects:
















