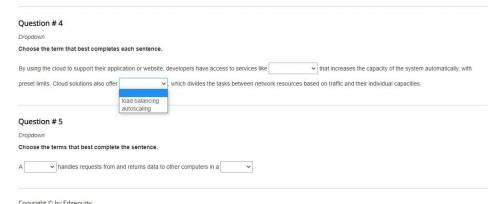
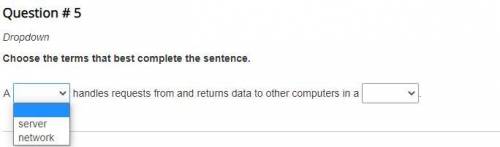
Same answers on both
...

Answers: 1
Other questions on the subject: Computers and Technology

Computers and Technology, 22.06.2019 04:30, Lilabbychichi
Ryan is working on the layout of her web page. she needs to figure out where her header, navigation bar, text, and images should go. what technique can her?
Answers: 1

Computers and Technology, 22.06.2019 10:40, Morghurley2000
"it security policy enforcement and monitoring" respond to the following: describe how monitoring worker activities can increase the security within organizations. describe the rationale that managers should use to determine the degree of monitoring that the organization should conduct. explain the extent to which you believe an organization has the right to monitor user actions and traffic. determine the actions organizations can take to mitigate the potential issues associated with monitoring user actions and traffic.
Answers: 3


Computers and Technology, 24.06.2019 20:00, impura12713
Avirus enters a computer or network as code embedded in other software directly from another computer
Answers: 1
Do you know the correct answer?
Questions in other subjects:

Mathematics, 14.12.2019 11:31

History, 14.12.2019 11:31


Biology, 14.12.2019 11:31

Social Studies, 14.12.2019 11:31


Chemistry, 14.12.2019 11:31

Mathematics, 14.12.2019 11:31

Biology, 14.12.2019 11:31