Computers and Technology, 17.10.2020 20:01, aloading6574
We define the following terms:
Lexicographical Order, also known as alphabetic or dictionary order, orders characters as follows:
For example, ball < cat, dog < dorm, Happy < happy, Zoo < ball.
A substring of a string is a contiguous block of characters in the string. For example, the substrings of abc are a, b, c, ab, bc, and abc.
Given a string, , and an integer, , complete the function so that it finds the lexicographically smallest and largest substrings of length .
Input Format
The first line contains a string denoting .
The second line contains an integer denoting .
Constraints
consists of English alphabetic letters only (i. e., [a-zA-Z]).
Output Format
Return the respective lexicographically smallest and largest substrings as a single newline-separated string.
Sample Input 0
welcometojava
3
Sample Output 0
ava
wel
Explanation 0
String has the following lexicographically-ordered substrings of length :
We then return the first (lexicographically smallest) substring and the last (lexicographically largest) substring as two newline-separated values (i. e., ava\nwel).
The stub code in the editor then prints ava as our first line of output and wel as our second line of output.
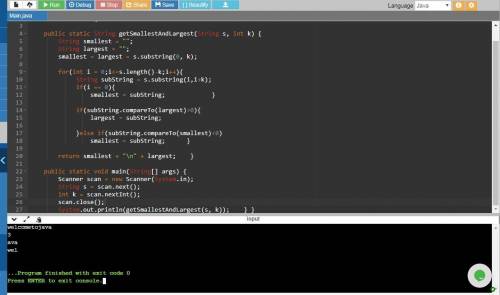
Solution:-
import java. util. Scanner;
public class Solution {
public static String getSmallestAndLargest(String s, int k) {
String smallest = "";
String largest = "";
smallest = largest = s. substring(0, k);
for (int i=1; i
String substr = s. substring(i, i+k);
if (smallest. compareTo(substr) > 0)
smallest = substr;
if (largest. compareTo(substr) < 0)
largest = substr;
}
return smallest + "\n" + largest;
}
public static void main(String[] args) {
Scanner scan = new Scanner(System. in);
String s = scan. next();
int k = scan. nextInt();
scan. close();
System. out. println(getSmallestAndLargest(s, k));
}
}

Answers: 2
Other questions on the subject: Computers and Technology

Computers and Technology, 22.06.2019 06:20, Masielovebug
In what kind of attack can attackers make use of millions of computers under their control in an attack against a single server or network availability confidentiality integrity identity automated attack software? those who wrongfully disclose individually identifiable health information can be fined up to what amount per calendar year? single most expensive malicious attack hipaa what are script kiddies? advanced persistent threat security manager security engineer what level of security access should a computer user have to do their job what process describes using technology as a basis for controlling the access and usage of sensitive data? cybercriminal
Answers: 1

Computers and Technology, 22.06.2019 08:40, batman48000
1. the program must provide following functions to extract some statistics. note that the data_list parameter specified in these functions may be the same for all functions or different for different functions—that is your choice. a skeleton file is provided on mirmir. a) open_file()prompts the user to enter a year number for the data file. the program will check whether the year is between 1990 and 2015 (both inclusive). if year number is valid, the program will try to open data file with file name ‘year. txt’, where is the year. appropriate error message should be shown if the data file cannot be opened or if the year number is invalid. this function will loop until it receives proper input and successfully opens the file. it returns a file pointer and year. i. hint: use string concatenation to construct the file name b) read_file(fp)has one parameter, a file pointer read. this function returns a list of your choosing containing data you need for other parts of this project. c) find_average(data_list) takes a list of data (of some organization of your choosing) and returns the average salary. the function does not print anything. hints: i. this is not the average of the last column of data. it is not mathematically valid to find an average by finding the average of averages—for example, in this case there are many more in the lowest category than in the highest category. ii. how many wage earners are considered in finding the average (denominator)
Answers: 1

Computers and Technology, 22.06.2019 17:00, Dweath50
1. so if i wanted to build a linux server for web services(apache) with 1cpu and 2 gb of memory.-operating at 75% of memory capacity2. a windows server with 2 cpu/ 4gb memory- operating at 85% of memory capacity3. a storage server with 1 cpu/ 2gb memory- operating at 85% of memory capacityhow much memory do i have to add for each server. so that the utilization rate for both cpu and memory is at a baseline of 60%."the details for the cpu like its processor or the memory's speed isnt to be concerned" yeah i kept asking my teacher if he's even sure about the but the whole class seems to be confused and the project is due in 3 days..this is a virtualization project where i have to virtualize a typical server into an exsi hypervisor.
Answers: 2
Do you know the correct answer?
We define the following terms:
Lexicographical Order, also known as alphabetic or dictionary order,...
Questions in other subjects:

Mathematics, 04.04.2021 06:50

Mathematics, 04.04.2021 06:50


Health, 04.04.2021 06:50

Mathematics, 04.04.2021 06:50

Chemistry, 04.04.2021 06:50