I need the answers for (b) and (c)
but I already know the 1st answer for (c) which is 'central'...

Computers and Technology, 05.05.2020 10:21, justttlearnnn12333
I need the answers for (b) and (c)
but I already know the 1st answer for (c) which is 'central' but don't know the rest
The remaining words for answers are 'backing', 'peripheral' and 'input'
PLEASE HELP
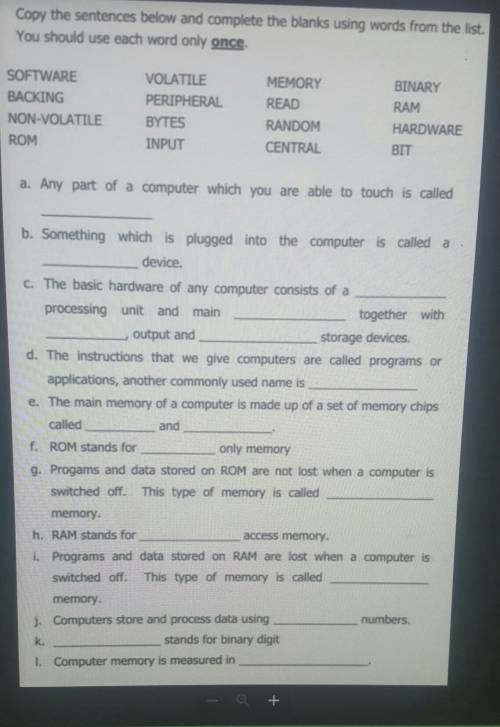

Answers: 2
Other questions on the subject: Computers and Technology

Computers and Technology, 22.06.2019 02:10, breanastone14
3. (5 points) describe what would be printed by the code below or what error would occur. const char* cstr = "0123456"; const char* ptr = & cstr[4]; cout < < ptr[-1] < < ptr < < endl; 1 4. (5 points) theseus has been trapped in a maze with a minotaur, which is trying to capture him. each round, theseus and the minotaur move through the maze; theseus towards the exit, and the minotaur towards theseus. theseus can move in any of the four cardinal directions, or he can wait for a round to see how the minotaur moves. write code that creates a data type to represent the possible moves that theseus could make.
Answers: 3

Computers and Technology, 22.06.2019 11:30, mmimay3501
What do character formats do for your document's message? a. set the tone b. provide organization c. provide clarity d. set how texts align with documents
Answers: 2

Computers and Technology, 23.06.2019 08:00, ionmjnm3041
The managing director of a company sends a christmas greeting to all his employees through the company email. which type of network does he use? he uses an .
Answers: 3

Computers and Technology, 23.06.2019 11:00, jolleyrancher78
What are the possible consequences of computer hacking? what is computer piracy? describe some examples. what are the effects of computer piracy? what are the possible consequences of computer piracy? what is intentional virus setting? describe some examples. what are the effects of intentional virus setting? what are the possible consequences of intentional virus setting? what is invasion of privacy? describe some examples. what are the effects of invasion of privacy? what are the possible consequences of invasion of privacy? what is an acceptable use policy and what is the purpose of the acceptable use policy what is intellectual property and how can you use it?
Answers: 1
Do you know the correct answer?
Questions in other subjects:

Arts, 03.12.2020 07:10

Mathematics, 03.12.2020 07:10

English, 03.12.2020 07:10





Mathematics, 03.12.2020 07:20


History, 03.12.2020 07:20






