R
o k 2015
traccens when users begin to yoe in the Toreld the name of an email recipient...

Computers and Technology, 05.05.2020 13:09, michaelswagout
R
o k 2015
traccens when users begin to yoe in the Toreld the name of an email recipient to whom they
the recents temat stress woms in the field
O the recients full contact information or as in a window
The botes son mas ad presents names to choose from
The stress
t r as and presents adresses to choose from
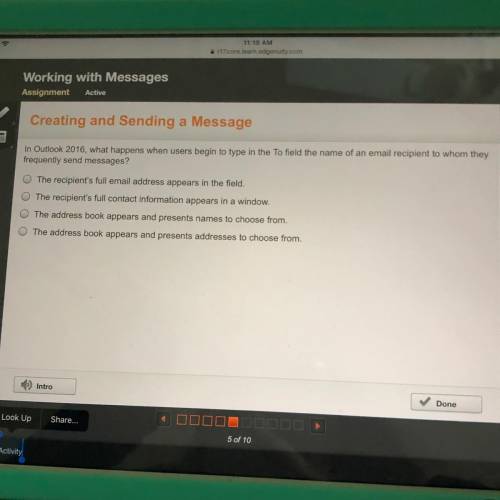

Answers: 2
Other questions on the subject: Computers and Technology


Computers and Technology, 22.06.2019 19:50, rosyposy43
Write a car class having two private member variables called tank and speed. write public methods called pumpgas and gofast. the method pumpgas gets an integer for gas that must be pumped. that value needs to be added to tank (no more than 20 gallons). it must return the amount of gas that is purchased ($4 per gallon). the method gofast should increase the speed by 5 each time it is called. write a constructor for the above class that initialized both variables to zero. write a tostring to display both the tank and speed when the car is printed. modify the car class to implement the interface comparable and an interface called carinter having the public methods in carinter. write the main program to create an array of size 5 of type car. create 5 car objects having each location of the array to refer to one of the cars. test the pumpgas, gofast, equals method on the array items. write an enhanced loop to print all the car values (using a tostring written last time).write a generic method to find the minimum of four items. pass int, double, char, string and car objects to test this method.
Answers: 1

Computers and Technology, 23.06.2019 03:10, kyleereeves2007
Acomputer has a two-level cache. suppose that 60% of the memory references hit on the first level cache, 35% hit on the second level, and 5% miss. the access times are 5 nsec, 15 nsec, and 60 nsec, respectively, where the times for the level 2 cache and memory start counting at the moment it is known that they are needed (e. g., a level 2 cache access does not even start until the level 1 cache miss occurs). what is the average access time?
Answers: 1

Computers and Technology, 23.06.2019 15:30, PlzNoToxicBan
The song about casey jones a railroad engineer who gives his life on the job would most likely gall under the folk song category of? a-work song b-nonsense song c-religious song d-ballad
Answers: 1
Do you know the correct answer?
Questions in other subjects:


Biology, 12.03.2021 21:00

Mathematics, 12.03.2021 21:00

Physics, 12.03.2021 21:00


English, 12.03.2021 21:00

Social Studies, 12.03.2021 21:00

Mathematics, 12.03.2021 21:00

Social Studies, 12.03.2021 21:00






