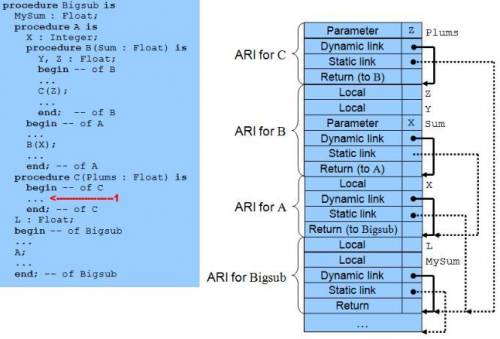
Show the stack with all activation record instances, including static and
dynamic chains, when...

Computers and Technology, 05.05.2020 22:03, phillipsalexis274
Show the stack with all activation record instances, including static and
dynamic chains, when execution reaches position 1 in the following skeletal
program. Assume Bigsub is at level 1.
procedure Bigsub is
MySum : Float;
procedure A is
X : Integer;
procedure B(Sum : Float) is
Y, Z : Float;
begin -- of B
. . .
C(Z)
. . .
end; -- of B
begin -- of A
. . .
B(X);
. . .
end; -- of A
procedure C(Plums : Float) is
begin -- of C
. . . <1
end; -- of C
L : Float;
begin -- of Bigsub
. . .
A;
. . .
end; -- of Bigsub

Answers: 1
Other questions on the subject: Computers and Technology

Computers and Technology, 22.06.2019 21:40, tdahna0403
Develop a function to create a document in the mongodb database “city” in the collection “inspections.” be sure it can handle error conditions gracefully. a. input -> argument to function will be set of key/value pairs in the data type acceptable to the mongodb driver insert api call b. return -> true if successful insert else false (require a screenshot)
Answers: 2

Computers and Technology, 23.06.2019 00:00, puppylove899
Which is the correct sequence of steps to set up a document in landscape orientation? a. select page setup from the file menu. then click the margins tab and select landscape. b. select page setup from the edit menu. then click the margins tab and select landscape. c. select page setup from the insert menu. then click the margins tab and select landscape. d. select page setup from the format menu. then click the margins tab and select landscape
Answers: 1


Computers and Technology, 24.06.2019 18:10, albattatasraap5wymy
Most information security incidents will occur because of select one: a. users who do not follow secure computing practices and procedures b. increases in hacker skills and capabilities c. poorly designed network protection software d. increasing sophistication of computer viruses and worms
Answers: 1
Do you know the correct answer?
Questions in other subjects:





Mathematics, 01.07.2019 05:30

Computers and Technology, 01.07.2019 05:30



Social Studies, 01.07.2019 05:30

Social Studies, 01.07.2019 05:30