Computers and Technology, 20.03.2020 00:05, krose5807
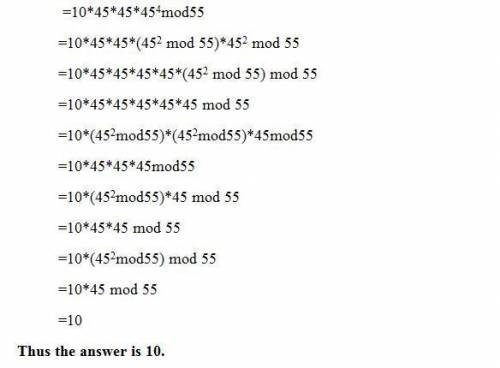
Given the RSA private key { d, n } = { 23, 55 }, use modulo reduction to decipher the message "10". You must show all steps and clearly state your answer to receive full credit.

Answers: 3
Other questions on the subject: Computers and Technology

Computers and Technology, 22.06.2019 01:00, zuleromanos
)a grad student comes up with the following algorithm to sort an array a[1..n] that works by first sorting the first 2/3rds of the array, then sorting the last 2/3rds of the (resulting) array, and finally sorting the first 2/3rds of the new array. 1: function g-sort(a, n) . takes as input an array of n numbers, a[1..n] 2: g-sort-recurse(a, 1, n) 3: end function 4: function g-sort-recurse(a, `, u) 5: if u ⒠` ≤ 0 then 6: return . 1 or fewer elements already sorted 7: else if u ⒠` = 1 then . 2 elements 8: if a[u] < a[`] then . swap values 9: temp ↠a[u] 10: a[u] ↠a[`] 11: a[`] ↠temp 12: end if 13: else . 3 or more elements 14: size ↠u ⒠` + 1 15: twothirds ↠d(2 ◠size)/3e 16: g-sort-recurse(a, `, ` + twothirds ⒠1) 17: g-sort-recurse(a, u ⒠twothirds + 1, u) 18: g-sort-recurse(a, `, ` + twothirds ⒠1) 19: end if 20: end function first (5 pts), prove that the algorithm correctly sorts the numbers in the array (in increasing order). after showing that it correctly sorts 1 and 2 element intervals, you may make the (incorrect) assumption that the number of elements being passed to g-sort-recurse is always a multiple of 3 to simplify the notation (and drop the floors/ceilings).
Answers: 3

Computers and Technology, 22.06.2019 19:10, sammigrace5820
How might the success of your campaign be affected if you haven’t carefully completed all field data or if you accidentally insert the wrong merge field in the document?
Answers: 1

Computers and Technology, 23.06.2019 14:30, bernicewhite156
Select the correct answer. what does it indicate when a website displays https instead of http? a. the website is secure. b. there is no secure sockets layer. c. the secure sockets layer is hidden. d. the website is not secure.
Answers: 1

Computers and Technology, 23.06.2019 15:00, ryleerose255
Idon’t understand the double8 coding problem. it is java
Answers: 1
Do you know the correct answer?
Given the RSA private key { d, n } = { 23, 55 }, use modulo reduction to decipher the message "10"....
Questions in other subjects:

Biology, 18.09.2020 14:01

Mathematics, 18.09.2020 14:01

Mathematics, 18.09.2020 14:01

Mathematics, 18.09.2020 14:01

French, 18.09.2020 14:01

Mathematics, 18.09.2020 14:01

Business, 18.09.2020 14:01

Mathematics, 18.09.2020 14:01

Mathematics, 18.09.2020 14:01

Mathematics, 18.09.2020 14:01