Computers and Technology, 24.02.2020 19:04, Mistytrotter
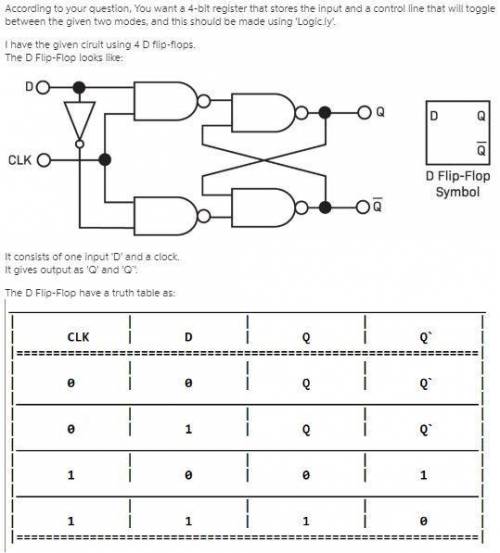
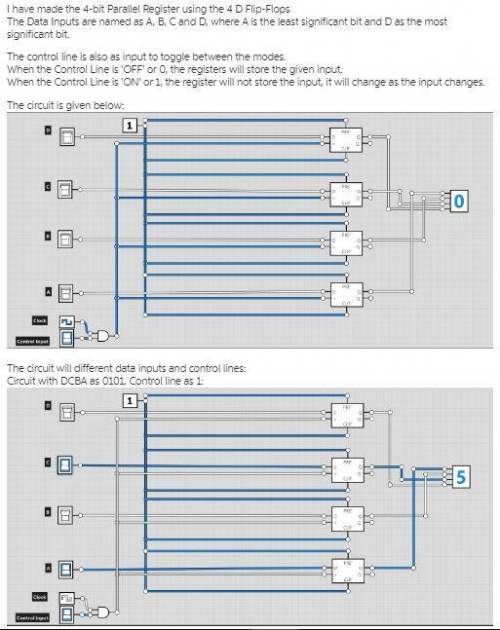
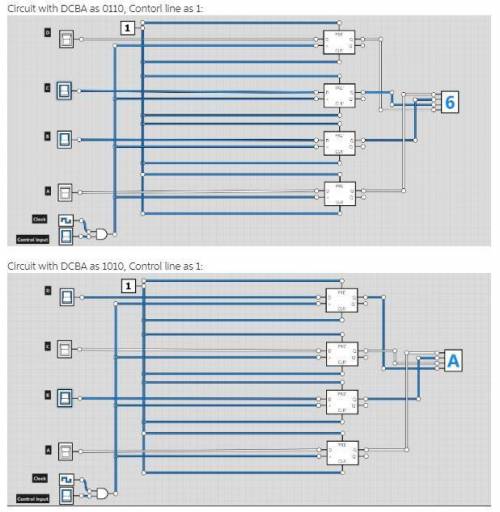
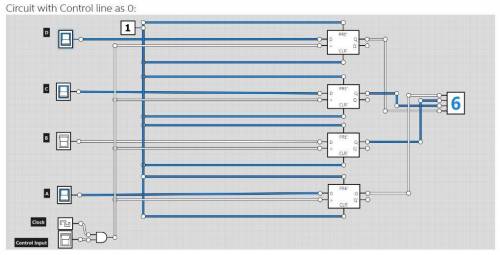
Design a 4-bit register that can accept an input from the user and store the accepted input. The 4-bit register will operate in two modes: 1) the data input is stored into the register, and 2) The register retains its past value and does not store the new value. To operate in these two states, the register should accept 5 inputs: 4 data inputs and 1 control input. If the control input is 0, the input is stored. Otherwise, the input is not stored.

Answers: 1
Other questions on the subject: Computers and Technology

Computers and Technology, 23.06.2019 16:30, vitothebest1
You have read about the beginnings of the internet and how it was created. what was the internet originally created to do? (select all that apply) share research. play games. communicate. share documents. sell toys
Answers: 1

Computers and Technology, 24.06.2019 12:00, log40
Jack is assisting his younger sibling mary with her mathematics assignment, which includes a study of the number system. jack explains to mary that whole numbers are counting numbers that could be used to record the number of fruits in a basket. which data type represents whole numbers? a. integers. b.floating-point numbers. c. strings. d.boolean
Answers: 1


Computers and Technology, 25.06.2019 09:20, sparkybig12
The technology acceptance model (tam) is a two-factor model that describes user acceptance of new or replacement technology solutions (davis, 1989). this evaluation model has withstood the test of time and is widely used. the model is based upon perceptions and beliefs of individuals and measures two types of factors: (a) perceived ease of use and (b) perceived usefulness. prepare an analysis (briefing paper) (5 to 7 strong paragraphs) in which you explain how cybersecurity researchers could use the tam model to explore the factors which affect employee acceptance of biometrics used for access to facilities and/or computing systems. what research questions might they ask? what measurements would be needed? post your briefing paper as a reply to this topic. remember to cite your sources (3 minimum) and include a reference list at the end of your posting.
Answers: 1
Do you know the correct answer?
Design a 4-bit register that can accept an input from the user and store the accepted input. The 4-b...
Questions in other subjects:


Mathematics, 12.03.2021 09:50

Physics, 12.03.2021 09:50

Mathematics, 12.03.2021 09:50


Mathematics, 12.03.2021 14:00

Mathematics, 12.03.2021 14:00



Mathematics, 12.03.2021 14:00