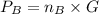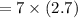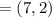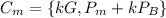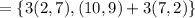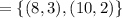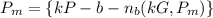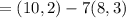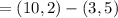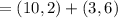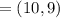This problem performs elliptic curve encryption/decryption using the scheme out-
lined in secti...

Computers and Technology, 02.01.2020 20:31, himatasy
This problem performs elliptic curve encryption/decryption using the scheme out-
lined in section 10.4. the cryptosystem parameters are e11(1,6) and g = (2,7). b's
secret key is nb = 3. (hint: note the relationship of this system to the one discussed in
the previous question (10.14)]
a. find b's public key pb.
b. a wishes to encrypt the message pm = (10,9) and chooses the random value
k = 4. determine the ciphertext cm.
c. show the calculation by which в recovers pm from cm.
(10.> for e11(1,6) consider the point g=(2,7). compute the multiple of g from 2g through 13g.)

Answers: 1
Other questions on the subject: Computers and Technology

Computers and Technology, 23.06.2019 15:20, manarhizam12
An ou structure in your domain has one ou per department, and all the computer and user accounts are in their respective ous. you have configured several gpos defining computer and user policies and linked the gpos to the domain. a group of managers in the marketing department need different policies that differ from those of the rest of the marketing department users and computers, but you don't want to change the top-level ou structure. which of the following gpo processing features are you most likely to use? a, block inheritance b, gpo enforcement c, wmi filtering d, loopback processing
Answers: 3

Computers and Technology, 23.06.2019 21:30, mariah10455
Write a fragment of code that reads in strings from standard input, until end-of-file and prints to standard output the largest value. you may assume there is at least one value. (cascading/streaming logic, basic string processing)
Answers: 3

Computers and Technology, 24.06.2019 01:00, cheycheybabygirl01
How can the temperature of a room be raised by 5degreesf?
Answers: 1

Computers and Technology, 24.06.2019 17:00, mrsrobinson1014
What are some examples of what can be changed through options available in the font dialog box? check all that apply. font family italicizing bolding pasting drop shadow cutting character spacing special symbols
Answers: 2
Do you know the correct answer?
Questions in other subjects:


Mathematics, 23.12.2020 20:50

English, 23.12.2020 20:50








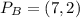 "(b) The ciphertext is "
"(b) The ciphertext is "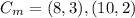 "(c) Between the two points, addition as well as multiplication are proceeding.
"(c) Between the two points, addition as well as multiplication are proceeding.