
Computers and Technology, 26.12.2019 00:31, babygirlgabby2137
One of the earlier applications of cryptographic hash functions was the storage
of passwords for user authentication in computer systems. with this method, a
password is hashed after its input and is compared to the stored (hashed) reference
password. people realized early that it is sufficient to only store the hashed versions
of the passwords.
1. assume you are a hacker and you got access to the hashed password list. of
course, you would like to recover the passwords from the list in order to impersonate
some of the users. discuss which of the three attacks below allow this.
exactly describe the consequences of each of the attacks:
attack a: you can break the one-way property of h.
attack b: you can find second preimages for h.
attack c: you can find collisions for h.
2. why is this technique of storing hashed passwords often extended by the use
of a so-called salt? (a salt is a random value appended to the password before
hashing. together with the hash, the value of the salt is stored in the list of hashed
passwords.) are the attacks above affected by this technique?
3. is a hash function with an output length of 80 bit sufficient for this application?

Answers: 2
Other questions on the subject: Computers and Technology

Computers and Technology, 23.06.2019 03:00, tay9122
Jason, samantha, ravi, sheila, and ankit are preparing for an upcoming marathon. each day of the week, they run a certain number of miles and write them into a notebook. at the end of the week, they would like to know the number of miles run each day, the total miles for the week, and average miles run each day. write a program to them analyze their data. your program must contain parallel arrays: an array to store the names of the runners and a two-dimensional array of five rows and seven columns to store the number of miles run by each runner each day. furthermore, your program must contain at least the following functions: a function to read and store the runners’ names and the numbers of miles run each day; a function to find the total miles run by each runner and the average number of miles run each day; and a function to output the results. (you may assume that the input data is stored in a file and each line of data is in the following form: runnername milesday1 milesday2 milesday3 milesday4 milesday5 milesday6 milesday7.)
Answers: 3

Computers and Technology, 23.06.2019 03:10, kyleereeves2007
Acomputer has a two-level cache. suppose that 60% of the memory references hit on the first level cache, 35% hit on the second level, and 5% miss. the access times are 5 nsec, 15 nsec, and 60 nsec, respectively, where the times for the level 2 cache and memory start counting at the moment it is known that they are needed (e. g., a level 2 cache access does not even start until the level 1 cache miss occurs). what is the average access time?
Answers: 1

Computers and Technology, 23.06.2019 10:00, thezbell
What is estimated time of arrival (eta)? a device that measures the acceleration (the rate of change of velocity) of an item and is used to track truck speeds or taxi cab speeds a gps technology adventure game that posts the longitude and latitude location for an item on the internet for users to find a north/south measurement of position the time of day of an expected arrival at a certain destination and is typically used for navigation applications
Answers: 3
Do you know the correct answer?
One of the earlier applications of cryptographic hash functions was the storage
of passwords f...
of passwords f...
Questions in other subjects:


Mathematics, 13.03.2021 02:10

Biology, 13.03.2021 02:10

Mathematics, 13.03.2021 02:10




Mathematics, 13.03.2021 02:10



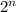 . It requires the attacker to have an idea about the kind of passwords that might be used and then brute force all of them to find string that has the same hash. Each try will have a chance of 1/
. It requires the attacker to have an idea about the kind of passwords that might be used and then brute force all of them to find string that has the same hash. Each try will have a chance of 1/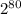 different hash values. This means there is at least one collision if
different hash values. This means there is at least one collision if 



